
- Автоматизация
- Антропология
- Археология
- Архитектура
- Биология
- Ботаника
- Бухгалтерия
- Военная наука
- Генетика
- География
- Геология
- Демография
- Деревообработка
- Журналистика
- Зоология
- Изобретательство
- Информатика
- Искусство
- История
- Кинематография
- Компьютеризация
- Косметика
- Кулинария
- Культура
- Лексикология
- Лингвистика
- Литература
- Логика
- Маркетинг
- Математика
- Материаловедение
- Медицина
- Менеджмент
- Металлургия
- Метрология
- Механика
- Музыка
- Науковедение
- Образование
- Охрана Труда
- Педагогика
- Полиграфия
- Политология
- Право
- Предпринимательство
- Приборостроение
- Программирование
- Производство
- Промышленность
- Психология
- Радиосвязь
- Религия
- Риторика
- Социология
- Спорт
- Стандартизация
- Статистика
- Строительство
- Технологии
- Торговля
- Транспорт
- Фармакология
- Физика
- Физиология
- Философия
- Финансы
- Химия
- Хозяйство
- Черчение
- Экология
- Экономика
- Электроника
- Электротехника
- Энергетика
Ақпараттық коммуникациялық технологиялар пәні бойынша барлық мамандық студенттеріне арналған тест тапсырмалары 1 страница
Ақ параттық коммуникациялық технологиялар пә ні бойынша барлық мамандық студенттеріне арналғ ан тест тапсырмалары
Кредит саны -3
Жалпы сұ рақ саны-500
Tests on ICT subject
Начало формы
. Key- for deleting the symbol to the left of the cursor:
A. Backspace
B. Shift
C. CapsLock
D. Delete
E. Space bar
. What sign writes after formula in spreadsheet?
after the sign =
after the space
after the number
after the sign #
after the sign " "
What program works with databases?
MS Access
MS PowerPoint
MS Word V
MS Explorer
MS Excel
. What programs are anti-virus:
Kaspersky, Doctor Web, Aidtest
MS Word, MS Excel, MS Access
ARJ, ZIP, RAR
MS PowerPoint
Microsoft Internet Explorer, Netscape Navigator
Select the file name anketa with expansion txt.
Anketa. txt
Anketa. txt.
Anketa / txt.
Anketa.. txt.
Anketa-txt
. program MS Excel is...
Spreadsheet
Database
Text editor
Graphics editor
Dictionary
. What maximum number has a name of file or folder in Windows?
. E-mail is
Electronic mail.
Work with text.
Database.
A game.
Testing tool.
. How many columns in Excel 2007 spreadsheet?
16385.
255.
289.
5.
65536.
. Tip archiver:
WinRar, WinZip
WinZip, MS DOS
UNIX, MS DOS
Aidtest, Doctor, Web
Aidtest, UNIX
. Translate the decimal system to hexadecimal: 555
22B
45B
20B
. What symbol replaces any number of any symbols?
*
?
\
?,
()
. How writes: " All files without exception"?
*. *
?.?
*.?
?
:
. What program designes to work in the Internet:
Internet Explorer
Microsoft Word
Microsoft Excel
Outlook Express
Microsoft Access
. Which extension has Excel document?
*. xls
*. pcx
*. cdr
*. bmp
*. txt
. What is the Windows program for viewing Web- pages?
Internet Explorer
Microsoft Word
Microsoft Access
Microsoft Excel
Outlook Express
. Add numbers 101 + 101
. Calculate 1011-111 in the binary system
. Translate number from decimal system to octal: 658
. Translate number from hexadecimal to decimal system: F53
. Storage Device
HDD
Power Supply
Mouse
Monitor
Keyboard
. What does it mean = SUM (A2: A5) in MS Excel
The summation contents of cells A2, A3, A4, A5.
Select cells from A2 to A5.
Dividing the value of the cell A2 to A5 cell value.
Summation A2 and A5 cell contents.
Highlight cells A2 and A5 block
Which of these programs is a graphical editor?
CorelDraw;
WinZip;
Microsoft Word;
AVP, Kaspersky;
DoctorWeb;
Enter the correct form of the address Internet site:
http: //www. mail. ru
htp: //www. mail. ru
http: //www. mail-ru
http / www. mail. -- ru
http: //www. mail
Which of the following Boolean operations recordes correctly
1 " and" 1 = 1
0 " or" 1 = 0
0 " and" 0 = 1
0 " and" 1 = 1
1 " and" 0 = 1
How calls document in Excel spreadsheet?
book
leaf
page
presentations
package
The formula means = A2 + B5:
Adds contents of cells B5 and A2
Specify a range of cells B5 and A2
Subtract the contents of cells B5 and A2
Subtract the contents of cell A2 B5 cell content
Highlights cells A2 and B5
. Selection E8:
column E line 8
A column of row 1
line in column 8
column E row 4
line 8
. the object that allows you to make a selection in MS Access:
Inquiry
Table
The form
Module
Macro
. Windows. How can you copy active window as a graphic element? ''
< Alt + Print Screen>
< Ctrl + C>
< Ctrl + V>
< Shift + F12>
< Ctrl + X>
. Formulu. How writes summation of cells from D2 to D7 in MS Excel:
= Sum (D2: D7)
= Sum (D2 \ D7)
= Sum (D2-D7)
= Sum (D2, D3, D7)
= Sum (D2, D7)
. The command for uncompress the file:
Extract.
View.
New.
Open Save.
Add.
How calls the coordinates of a cell in Excel spreadsheet?
Address.
Cell.
Letter.
Numeral
Room.
. What is used for connecting Computer to the LAN
Servers.
Network adapter.
Network filters.
Topolpgii network.
Cable.
. Which expansion has document in Power Point 2007?
*. ppt
*. txt
*. pcx
*. bmp
*. xls
. Function " Minimum value" in Excel is:
MIN
ZNACHMIN
MINE
MINZNACH
MAX
. Function " Maximum value" in Excel is:
MAX
MIN
ZNACHMIN
MINE
MINZNACH
. Choose the correct answer of e-mail address:
KasGMA@astana. kz
KasGMA @. kz
@ Astana. kz KasGMA
KasGMA. astana. @.
KasGMA. astana. kz
Calculating by the formula in Excel " = B1 * C1-B2 / A2", if
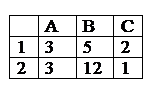
13/4
-7
-13/4
Result of sum 1+0=?
0, 1
Find determinant =МОПРЕД (A1: C3)?
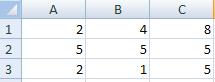
-60
-30
. Find determinant =МОПРЕД (A1: C3)?
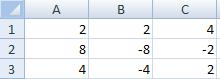
-96
-86
. Find determinant =МОПРЕД (A1: C3)
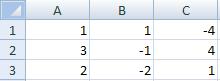
-45
-25
. Find determinant =МОПРЕД (A1: C3)?
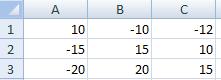
-1
-2
. Find determinant =МОПРЕД (A1: C3)?
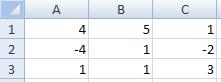
-65
-64
. Find determinant =МОПРЕД (A1: C3)?
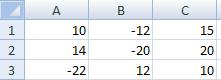
-1520
-2400
-2020
. What domen is used in RK?
kz
uz
su
fr
ru
calculate =SIN (B1) / COS(B1)?
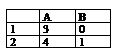
-1
. calculate " =B1^C1-B2/A2"?
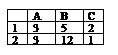
13/4
-7
-13/4
. result of =ОКРУГЛ(А2, 1)?
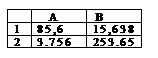
3, 8
3, 7
3, 75
3, 76
3, 756
. calculate numbers by this function =СР3НАЧ(А1: D2)
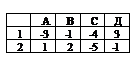
-1
-8
calculate numbers by this function =ABS(A1)+ABS(B1)-A2*B2

-64
-4
. Find determinant =МОПРЕД (A1: C3)?
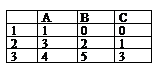
-1
. Find determinant =МОПРЕД (A1: C3)?
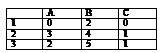
-2
-1
5
. Find determinant =МОПРЕД (A1: C3)?
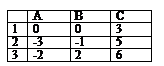
-24
-12
-8
. Find determinant =МОПРЕД (A1: C3)?
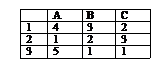
-20
-35
. Find determinant =МОПРЕД (A1: C3)?
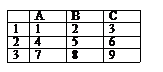
. Find determinant =МОПРЕД (A1: C3)?
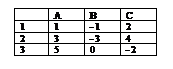
-38
-10
. Find determinant =МОПРЕД (A1: C3)?
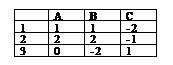
-14
. Find determinant =МОПРЕД (A1: C3)?
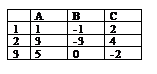
-10
-38
. Find determinant =МОПРЕД (A1: C3)?

-14
. Find determinant =МОПРЕД (A1: C3)?
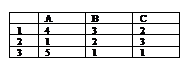
-20
. Find determinant =МОПРЕД (A1: C3)?
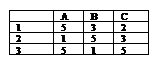
-20
-35
. Find the right expansion of sound file
*. AVI, *. MID, *. WAV
*AVI, *MID, *TXT,
*. BMP *AVI, *MID, *. DOC
*AVI, *MID, *. WAV, *. BMP, *. DOC
*AVI, *TXT, *. WWW, *. BMP, *. DOC
1. CD-ROM stands for:
Compactable Disk Read Only Memory
Compact Data Read Only Memory
Compactable Read Only Memory
Compact Disk Read Only Memory
CD Drive
2. Which device is required for the Internet connection?
Modem
Joystick
CD Drive
NIC Card
Printers
6. CPU contains:
control unit and an arithmetic logic unit
analytical engine and a control unit
card reader anda printing device
arithmetic logic unit and a card reader
compact Disk Read Only Memory
10. Which technology is used in a CDROM Drive?
Optical
Mechanical
Electromechanical
Fiber Optical
Driver
11. The analytical Engine developed during First Generation of computers used.... as a memory unit:
Counter Wheels
RAM
Cards
Floppies
Driver
13. WAN stands for:
Wide Area Network
Wap Area Network
Wide Array Net
Wireless Area Network
Disk memory
17. Second Generation computers were developed during:
1956-1965
1949-1955
1965-1970
1970-1990
1986-1999
19. A collection of related files is called a....
database
field
character
record
network
1. What menu is selected to print?
File
Special
Edit
Tools
None of these
15. The......... performs simple mathematics for the CPU.
ALU
DIMM
BUS
Register
None of these
What is e-commerce? 
Buying and selling products and services over the Internet
Buying and selling computer products
Buying and selling products and services not found in stores
Buying and selling international goods
Buying and selling computer software
76. Antispyware
a) is a type of security software designed to identify and neutralize Web bugs, ad-serving cookies, and other spyware.
b) claim that the datain their cookies is used simply to select and display ads that might interestyou.
c) to prevent ads from appearing on their screens.
d) which uses an intermediary, or proxy, serverto relay Web page requests after masking the originatingIP address
e) Online storefronts offergoods, merchandise, andservicesto consumers.
77. bannerad
a) is an advertisementembedded at the top of a Web page.
b) Businesses sell goods and services to other businessesor to the government.
c) Consumers sell to each other at popular auction and list sites such as eBay and
d) craigslist.
e) the number of times that site visitors click the ad to connect to theadvertiser’s site.
f) (technically an HTTP cookie) is a smallchunk of data generated by a Web server and stored in a text file on yourcomputer’s hard disk.
78. When the HTML source document that’s received by your local browser handles interactions, the process is referred to
a) client-side
b) cookie
c) e-commerce
d) e-mail account
e) e-mail address
79. cookie
a) (technically an HTTP cookie) is a small chunk of data generated by a Web server and stored in a text file on your computer’s hard disk.
b) the number of times that site visitors click the ad to connect to theadvertiser’s site.
c) Businesses sell goods and services to other businessesor to the government.
d) is an advertisementembedded at the top of a Web page.
e) Consumers sell to each other at popular auction and list sites such as eBay and
80. e-commerce
a) typically refers to business transactionsthat are conducted electronically over a computer network.
b) gets your electronicmailbox set up on an e-mail server.
c) is an electronicdocument transmitted over a computer network.
d) a computerthat essentially acts as a central post office for a group of people.
e) is created by the Web sitethat you are visiting.
81. Whether you use local e-mail or Webmail, your e-mail account has a unique
a) e-mail address
b) hover ad
c) Flash cookie
d) first-party cookie
e) e-mail server
82 The software you use to send, receive, and manage messages is called
a) e-mail client software
b) hover ad
c) Flash cookie
d) first-party cookie
e) e-mail server
83. e-mail message
a) is an electronic document transmitted over a computer network.
b) gets your electronicmailbox set up on an e-mail server.
c) typically refers to business transactions that are conducted electronically over a computer network
d) a computer that essentially acts as a central post office for a group of people.
e) is created by the Web site that you are visiting.
84. The computers and software that provide e-mail services form an
a) e-mail system.
b) e-mail client software
c) hover ad
d) Flash cookie
e) first-party cookie
85. e-mail server
a) a computerthat essentially acts as a central post office for a group of people.
b) is an electronic document transmitted over a computer network.
c) gets your electronicmailbox set up on an e-mail server.
d) typically refers to business transactions that are conducted electronically over a computer network
e) is created by the Web site that you are visiting.
86. HTML
a) (Hypertext Markup Language) is a setof specifications for creating documents that a browser can displayas a Web page.
b) also called a local sharedobject, is the Flash equivalent of a conventional Web cookie.
c) overlays thecontent on a Web page, sometimes obscuring it until you click the ad or itstimer expires and the ad disappears.
d) adds HTML tags to a document, spreadsheet, or other text-based file to create an HTML document that can bedisplayed by a browser.
e) which is similar to a word processing file, but hasan. htm or. html extension.
87. HTML document
a) which is similar to a word processing file, but hasan. htm or. html extension.
b) (Hypertext Markup Language) is a setof specifications for creating documents that a browser can displayas a Web page.
c) also called a local sharedobject, is the Flash equivalent of a conventional Web cookie.
d) overlays thecontent on a Web page, sometimes obscuring it until you click the ad or itstimer expires and the ad disappears.
e) adds HTML tags to a document, spreadsheet, or other text-based file to create an HTML document that can bedisplayed by a browser.
88. HTTP
a) is a protocol that works with TCP/IPto get Web resources to your desktop.
b) uses the < form> tagto accept typed input.
c) is aterm used for e-mail messages containing HTML tags that produce bold, italicized, and underlined text; fancy fonts; embedded graphics; and variousfont sizes.
d) that specify how the document should appear when displayedon a computer screen or printed.
e) the current version was introduced in 2010.
89. hypertext
a) to describe a computer system that could storeliterary documents, link them according to logical relationships, and allow readers to comment and annotate what they read.
b) that indicateswhether the browser’s request could be fulfilled.
c) local e-mail.
d) InternetMessage Access Protocol) are used to manage your incoming mail.
e) is commonly used to addlogic and other programmable elements to a Web page.
90. When using a browser, you can access aWeb page by clicking a
a) Hypertextlink
b) local e-mail.
c) Link popularity
d) Keyword stuffing
e) JavaScript
91. persistent HTTP connection
a) reuses the same HTTP connection tosend and receive multiple requests.
b) (Multipurpose Internet Mail Extensions)provides a clever way of disguising digitalphotos, sounds, and other mediaas plain ASCII code that can travel over the Internet with text-based e-mail data.
c) is online jargon for Internet etiquette.
d) a cyberspace version of the metal cart you wheel around a store and fill up with merchandise.
e) sometimes called a P2P payment, an online payment, or a third party payment) offers an alternative to credit cards.
92. Pharming
a) is an exploit that redirects usersto fake sites by poisoning a domain name server with a false IP address.
b) is an e-mail based scam that’s designed to persuade you to reveal confidential information such as your bank account number or Social Security number.
c) is a program that extends a browser’s ability to work with file formats.
d) (Post Office Protocol version 3) used to manage your incoming mail.
e) is an advertisement that appears in a separate window when you connect to a Web page.
93. Phishing
a) is an e-mail based scam that’s designed to persuade you to reveal confidential information such as your bank account number or Social Security number.
b) is an exploit that redirects users to fake sites by poisoning a domain name server with a false IP address.
c) is a program that extends a browser’s ability to work with file formats.
d) (Post Office Protocol version 3) used to manage your incoming mail.
e) such as the one in Figure7-29, is an advertisement that appears in a separate window when you connect to a Web page.
94. query processor
a) looks for your search terms in thesearch engine’s indexed database and returns a list of relevant Web sites.
b) is software that pulls keywords from a Web page and stores themin an index database.
c) symbol that describes a relationship between search terms and therebyhelps you create a more focused query.
d) encrypts the data transmitted between your computer and a Website.
e) are symbols suchas: -) that represent emotions.
95. search engine indexer
a) is software that pulls keywords from a Web page and stores themin an index database.
b) looks for your search terms in thesearch engine’s indexed database and returns a list of relevant Web sites.
c) symbol that describes a relationship between search terms and therebyhelps you create a more focused query.
d) encrypts the data transmitted between your computer and a Website.
e) are symbols such as: -) that represent emotions.
96. search operator is a word or
a) symbol that describes a relationship between search terms and there by helps you create a more focused query.
b) looks for your search terms in thesearch engine’s indexed database and returns a list of relevant Web sites.
c) is software that pulls keywords from a Web page and stores themin an index database.
d) encrypts the data transmitted between your computer and a Website.
e) are symbols suchas: -) that represent emotions.
97. Smileys
a) are symbols suchas: -) that represent emotions.
b) encrypts the data transmitted between your computer and a Website.
c) looks for your search terms in thesearch engine’s indexed database and returns a list of relevant Web sites.
d) is software that pulls keywords from a Web page and stores themin an index database.
e) symbol that describes a relationship between search terms and therebyhelps you create a more focused query.
98. SMTP
a) (Simple Mail Transfer Protocol) handles outgoing mail.
b) is an abstract concept that represents one end of a connection.
c) because it is the source of the HTML tags used to construct a Web page.
d) unwanted electronic junk mail about medical products, low-cost loans, and fake software upgrades that arrives in your online mailbox.
e) is a type of utility software that captures unsolicitede-mail messages before they reach your Inbox.
99. Socket
a) is an abstract concept that represents one end of a connection.
b) (Simple Mail Transfer Protocol) handles outgoing mail.
c) because it is the source of the HTML tags used to construct a Web page.
d) unwanted electronic junk mail about medical products, low-cost loans, and fake software upgrades that arrives in your online mailbox.
e) is a type of utility software that captures unsolicitede-mail messages before they reach your Inbox.
100. sourcedocument
a) because it is the source of the HTML tags used to construct a Web page.
b) (Simple Mail Transfer Protocol) handles outgoing mail.
c) is an abstract concept that represents one end of a connection.
d) unwanted electronic junk mail about medical products, low-cost loans, and fake software upgrades that arrives in your online mailbox.
e) is a type of utility software that captures unsolicitede-mail messages before they reach your Inbox.
101. spam
a) unwanted electronic junk mail about medical products, low-cost loans, and fake software upgrades that arrives in your online mailbox.
b) (Simple Mail Transfer Protocol) handles outgoing mail.
c) is an abstract concept that represents one end of a connection.
d) because it is the source of the HTML tags used to construct a Web page.
e) is a type of utility software that captures unsolicitede-mail messages before they reach your Inbox.
102. spam filter
a) is a type of utility software that captures unsolicitede-mail messages before they reach your Inbox.
b) (Simple Mail Transfer Protocol) handles outgoing mail.
c) is an abstract concept that represents one end of a connection.
d) because it is the source of the HTML tags used to construct a Web page.
e) unwanted electronic junk mail about medical products, low-cost loans, and fake software upgrades that arrives in your online mailbox.
103. TLS
a) (Transport Layer Security) protocol that encrypt data travelingbetween a client computer and an HTTP server.
b) (Secure Sockets Layer) protocol that encrypt data travelingbetween a client computer and an HTTP server.
c) is one that is set by an affiliated site.
d) (short for World Wide Web) is a collection of document, image, video, and sound files that can be linked and accessed over the Internet using a protocol called HTTP.
e) or HTML editors, which provid es tools specifically designed to enter and format Web page text, graphics, and links.
104. Web
a) (short for World Wide Web) is a collection of document, image, video, and sound files that can be linked and accessed over the Internet using a protocol called HTTP.
b) (Secure Sockets Layer) protocol that encrypt data travelingbetween a client computer and an HTTP server.
c) is one that is set by an affiliated site.
d) (Transport Layer Security) protocol that encrypt data travelingbetween a client computer and an HTTP server.
e) or HTML editors, which providestools specifically designed to enter and format Web page text, graphics, and links.
105. Web authoring software
a) or HTML editors, which providestools specifically designed to enter and format Web page text, graphics, and links.
b) (Secure Sockets Layer) protocol that encrypt data travelingbetween a client computer and an HTTP server.
c) is one that is set by an affiliated site.
d) (Transport Layer Security) protocol that encrypt data travelingbetween a client computer and an HTTP server.
e) (short for World Wide Web) is a collection of document, image, video, and sound files that can be linked and accessed over the Internet using a protocol called HTTP.
106. Webbrowser
a) (commonly referred to asa browser) is client software thatdisplays Web page elements andhandles links between pages.
b) (also called a clear GIF or pixel tag) is a 1x1 pixel graphic embedded in a Web page or an e-mail message.
c) (also referred to as a Webspider) is a computer program that is automated to methodically visit Websites.
d) is the product or output of oneor more Web-based files displayed in a format similar to a page in a book.
e) (commonlyreferred to simply as a search engine) is a program designed to help peoplelocate information on the Web by formulating simple queries consistingof one or more words called keywords or search terms.
107. Web bug
a) (also called a clear GIF or pixel tag) is a 1x1 pixel graphic embedded in a Web page or an e-mail message.
b) (commonly referred to asa browser) is client software thatdisplays Web page elements andhandles links between pages.
c) (also referred to as a Webspider) is a computer program that is automated to methodically visit Websites.
d) is the product or output of oneor more Web-based files displayed in a format similar to a page in a book.
e) (commonlyreferred to simply as a search engine) is a program designed to help peoplelocate information on the Web by formulating simple queries consistingof one or more words called keywords or search terms.
108. Web crawler
a) (also referred to as a Webspider) is a computer program that is automated to methodically visit Websites.
b) (commonly referred to asa browser) is client software thatdisplays Web page elements andhandles links between pages.
c) (also called a clear GIF or pixel tag) is a 1x1 pixel graphic embedded in a Web page or an e-mail message.
d) is the product or output of oneor more Web-based files displayed in a format similar to a page in a book.
e) (commonlyreferred to simply as a search engine) is a program designed to help peoplelocate information on the Web by formulating simple queries consistingof one or more words called keywords or search terms.
109. Web page
a) is the product or output of oneor more Web-based files displayed in a format similar to a page in a book.
b) (commonlyreferred to simply as a search engine) is a program designed to help peoplelocate information on the Web by formulating simple queries consistingof one or more words called keywords or search terms.
c) is an Internet-based computer that accepts requests from browsers.
d) typically contains a collection of related information organized and formatted so it can be accessed using software called a browser.
e) is a markup language very similar to HTML, but it can becustomized with tags that describe the data in databases.
110. Web search engine
a) (commonlyreferred to simply as a search engine) is a program designed to help peoplelocate information on the Web by formulating simple queries consistingof one or more words called keywords or search terms.
b) is the product or output of oneor more Web-based files displayed in a format similar to a page in a book.
c) is an Internet-based computer that accepts requests from browsers.
d) typically contains a collection of related information organized and formatted so it can be accessed using software called a browser.
e) is a markup language very similar to HTML, but it can becustomized with tags that describe the data in databases.
|
|
|
© helpiks.su При использовании или копировании материалов прямая ссылка на сайт обязательна.
|